Problem: Driver will not install silently.
When trying to complete a silent install of a vendor supplied MSI that comes bundled with drivers, a window is shown during install prompting for input to continue with the install. The window shown also gives you the option to trust that publisher for future installs.
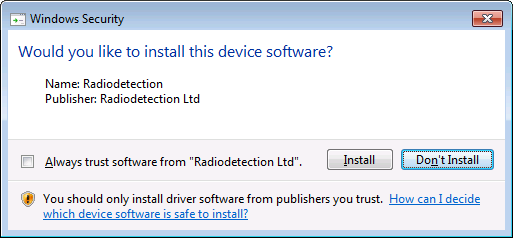
Reason: The certificate has gone past it's expiration date.
The reason why the Windows Security prompt is displayed is because the certifcate that was used to sign the .cat catalog file has gone past it's expiration date.
Fix: Add the certificate as a Trusted Publisher.
Adding the certificate into the certificate store within the Trusted Publisher folder will then allow any drivers from that publisher/vendor to install without any security prompts. Ticking the box on the "Would you like to install this device software" window has the same outcome.
Instructions:
Firstly we need to run through an install of the application so we can obtain a copy of the certifcate to use as a trusted publisher section of the certificate store. I completed this task in a VM on my test environment.
1. In your test environment complete an install of the application making sure to tick the 'Always trust software from ......' box and choose 'Install' on the Windows Security prompt.
2. Run certmgr.msc or open the certifcate manager however you like, navigate and expand the trusted publisher section on the left then click certificates underneath it.
3. You should see the certificate with the same name as from the Windows Security prompt (if you don't and you had the certificate store open while doing the install you just need to refresh the store, otherwise you will need to troubleshoot as to why).
4. Right click the certificate and choose 'All Tasks - Export' leaving everything as default save to a known location with a relevant filename, I'll use mycert.cer as the example for this.
Now that we have a copy of the certificate we just need to get the MSI to install the certificate in the trusted publisher section prior to the driver being installed. If like myself you are doing this with a vendor supplied MSI you will need to create a .mst transform file to make the changes to the MSI, I'm using Installshield but the process can be tailored for whatever tool you're using.
5. Add the certifcate you exported above to your transform (choosing either to compress the extra file into a cab or leave uncompressed, I added mine to a component that installs to the INSTALLDIR.
6. For the install the position of the 'Install Exec Sequence' may be different to my example, it depends on what method the vendor MSI ha used to install the drivers. If the 'MsiProcessDrivers' action is present in the sequence you will probably have to move it so that it occurs after we add the certificate.
7. We'll need to create a custom action for install and another to un-install as per the tables below - both need be 'New EXE - Path referencing a directory'.
| NAME - InstallCert | |
| *Action* | |
| Working Directory | INSTALLDIR |
| File Name & Command Line | certutil -addstore "TrustedPublisher" "[INSTALLDIR]mycert.cer" |
| Return Processing |
Synchronous (Ignores exit code) |
| In-Script Execution | Deferred Execution in System Context |
| *Sequence* | |
| Install Exec Sequence |
After InstallFiles |
| Install Exec Condition |
NOT Installed |
| NAME - UnInstallCert | |
| *Action* | |
| Working Directory | INSTALLDIR |
| File Name & Command Line | certutil -delstore "TrustedPublisher" "[INSTALLDIR]mycert.cer" |
| Return Processing |
Synchronous (Ignores exit code) |
| In-Script Execution | Deferred Execution in System Context |
| *Sequence* | |
| Install Exec Sequence |
After SelfUnregModules |
| Install Exec Condition |
REMOVE="ALL" |
8. Save and compile the MSI.
You can easily test whether your custom actions are working by completing an install and checking the trusted publishers section in the certificate manager..........or just complete an install and see if you're prompted by the Windows Security dialog.
